Do you want to make your project safer?
Submit an audit request and find out what results you will get with our team

Cyber Security Audit:
Analyzing your project and identifying all digital vulnerabilities
Analyzing your project and identifying all digital vulnerabilities
Avoid Data Leakage - sign up for a FREE consultation





Whitespots — a team
Whitespots specializes in identifying and analyzing vulnerabilities in digital platforms.
Our team of experts focuses on finding problems in financial software, internet portals, user-facing services, and mobile applications. We have developed a specialized portal
for vulnerability detection that includes more than 20 powerful scanners.
Our goal is to use our expertise and the developed platform in conjunction to prevent cyberattacks and ensure you the safety of your customers data. Every audit we perform has the potential to prevent millions of dollars in losses due to possible information leaks.
Our team of experts focuses on finding problems in financial software, internet portals, user-facing services, and mobile applications. We have developed a specialized portal
for vulnerability detection that includes more than 20 powerful scanners.
Our goal is to use our expertise and the developed platform in conjunction to prevent cyberattacks and ensure you the safety of your customers data. Every audit we perform has the potential to prevent millions of dollars in losses due to possible information leaks.



of security experts
By choosing
Whitespots,
you will get:

A report detailing all vulnerabilities and their levels of criticality
Manual and automated vulnerability discovery for digital products
Building a process of scanning repositories, domains, and Docker images for vulnerabilities
Working out the process with the company's product owners
We will provide guidance
to your team on the stages
of vulnerability remediation
to your team on the stages
of vulnerability remediation

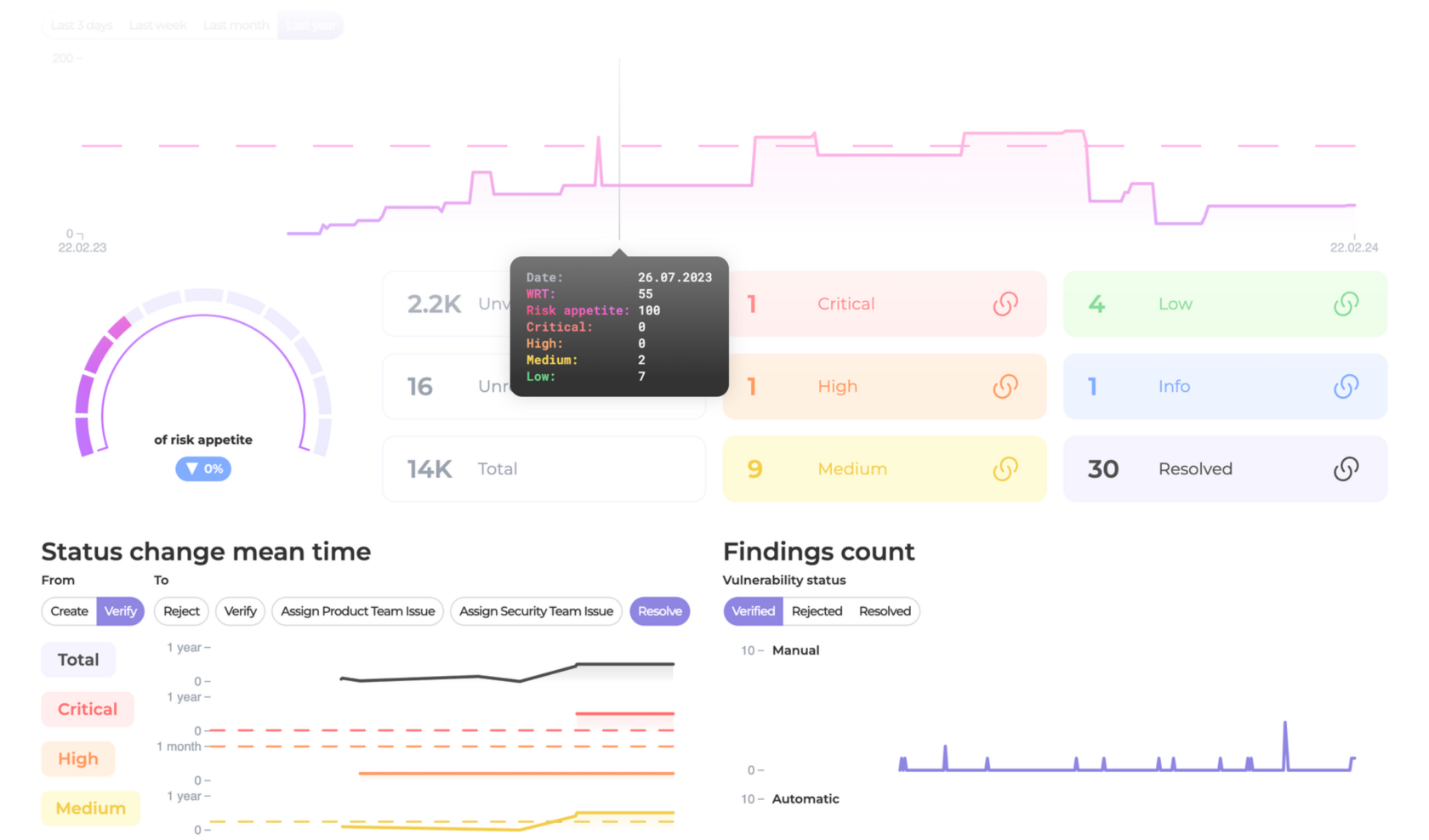
After the review, you will receive a comprehensive report detailing
all identified vulnerabilities and recommendations for their remediation.
If required, we are also available to conduct additional security assessments free of charge
all identified vulnerabilities and recommendations for their remediation.
If required, we are also available to conduct additional security assessments free of charge
32%



Sign up for a free
consultation
consultation
If you have any questions regarding applications security,
please leave a message
and our experts will be happy to assist you
please leave a message
and our experts will be happy to assist you
Benefits of working
We don't just help to detect vulnerabilities before they become
a problem. We provide your business with a platform
for vulnerability scanning and analysis. And we train your team
to use it, in order to automate all processes in the future
a problem. We provide your business with a platform
for vulnerability scanning and analysis. And we train your team
to use it, in order to automate all processes in the future
with Whitespots
Protection against reputational damage and financial losses
Our security checks help to prevent cyber attacks and loss of confidential customer data. This will ensure the safety of the company's reputation and financial resources






Automation of the Process: We Reduce Costs and Time
By integrating our portal into the company's software development life-cycle, vulnerability scanning, creating Jira tasks, finding duplicates, and other processes will become automatic. This will help to reduce the headcount and save hundreds of working hours every month.
In addition, our platform tracks vulnerabilities, allowing your developers
to focus on more critical tasks. This makes information security work more efficient
In addition, our platform tracks vulnerabilities, allowing your developers
to focus on more critical tasks. This makes information security work more efficient
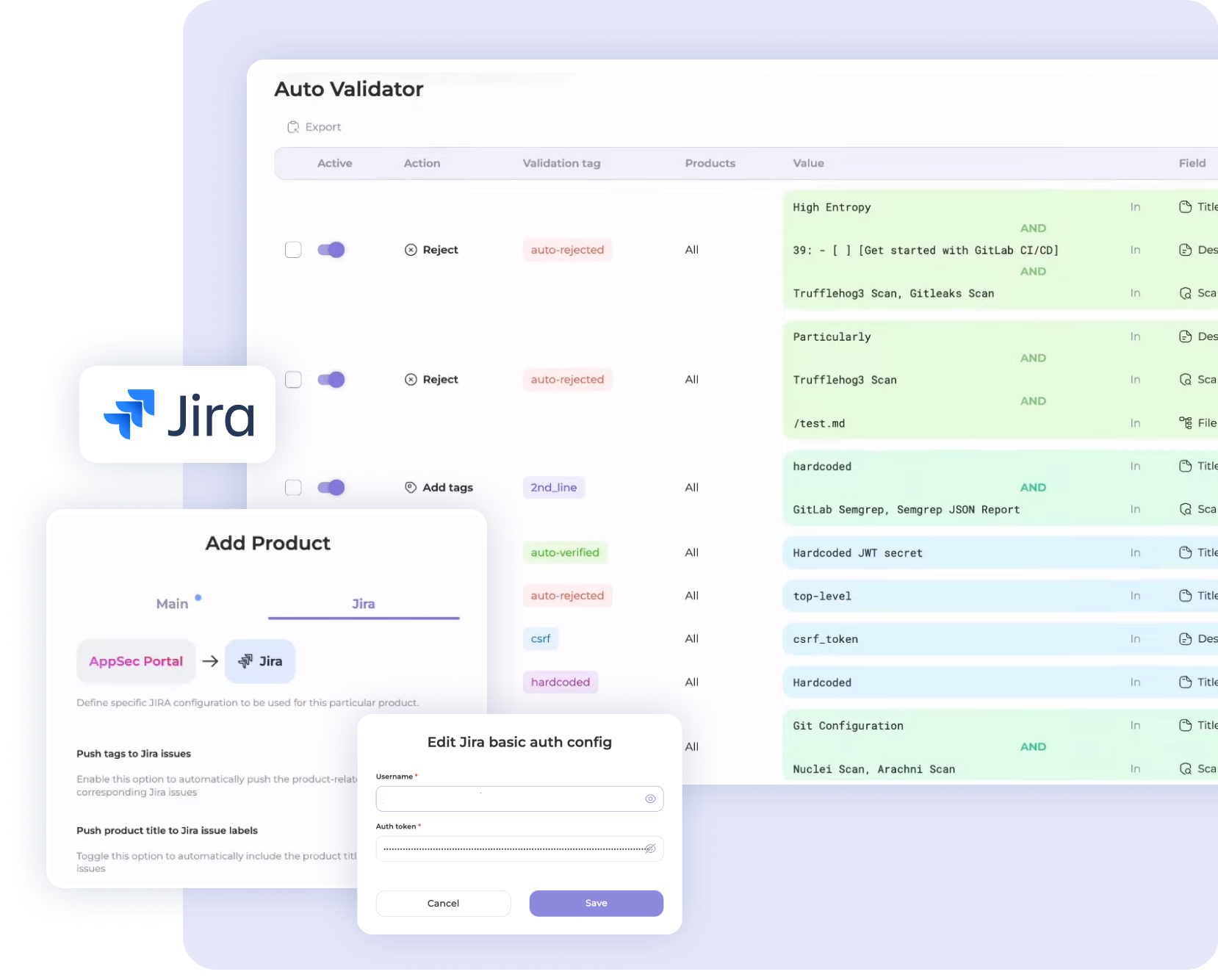
|
The service includes more than 20 scanners and supports third-party connections
Integrated with Jira — tasks go there immediately and are tracked there
Comprehensive analysis
The platform supports various report formats and is integrated with a wide range of popular scanners, including code scanners, secret scanners, web scanners, and many others.
With the help of Whitespots portal, you can even conduct scheduled checks of all your IT resources
With the help of Whitespots portal, you can even conduct scheduled checks of all your IT resources
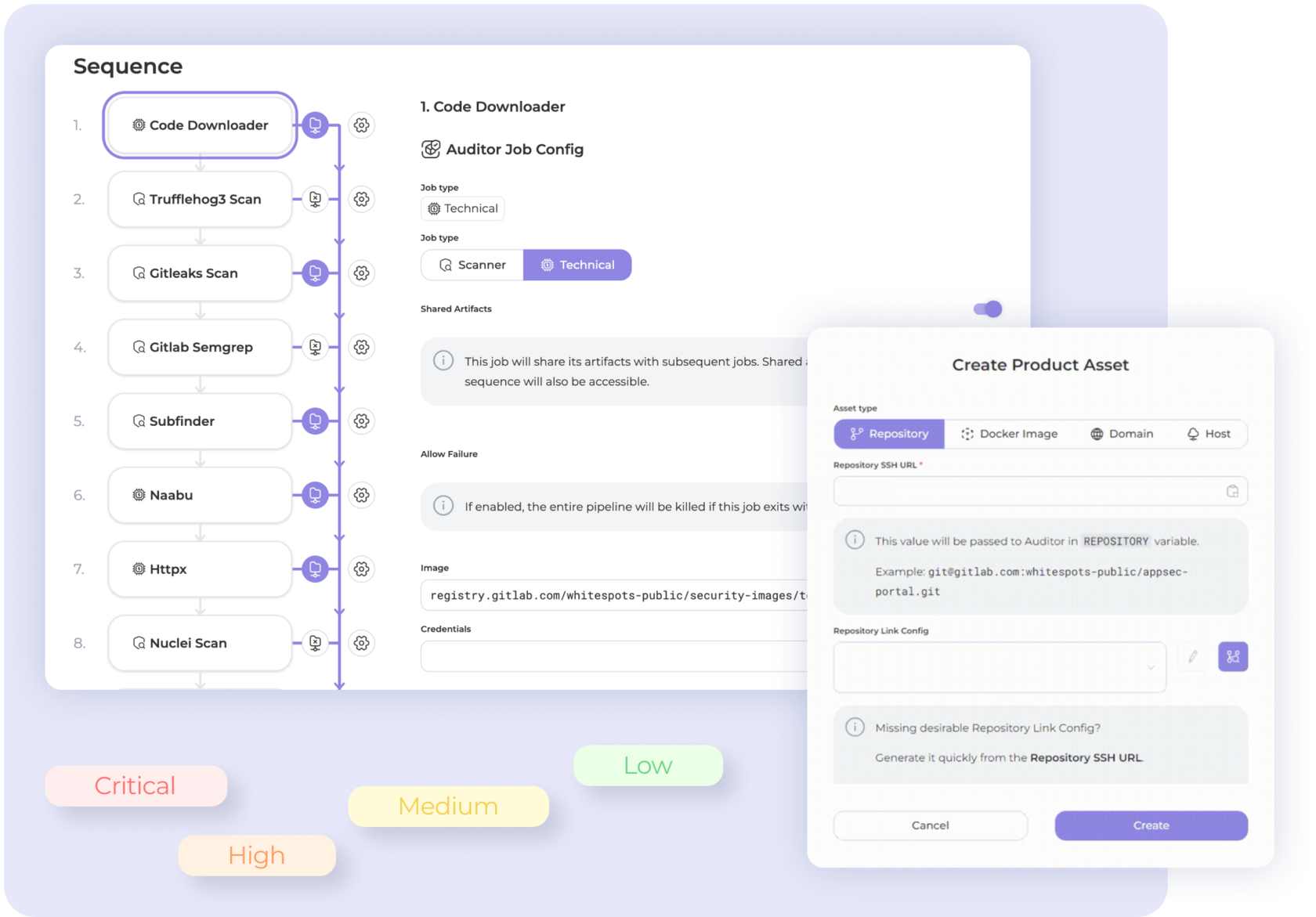


We scan all type of assets — from repositories to hosts
Task prioritization: we will show you which vulnerabilities
require more attention
require more attention
Implementation of a convenient
interface
interface
Installing our service is quick and easy. You will have 24 hours monitoring
of the safety status of your product.
Additionally, we offer a detailed guide to our platform and updates in a timely manner so that you are aware of the latest version
of the safety status of your product.
Additionally, we offer a detailed guide to our platform and updates in a timely manner so that you are aware of the latest version
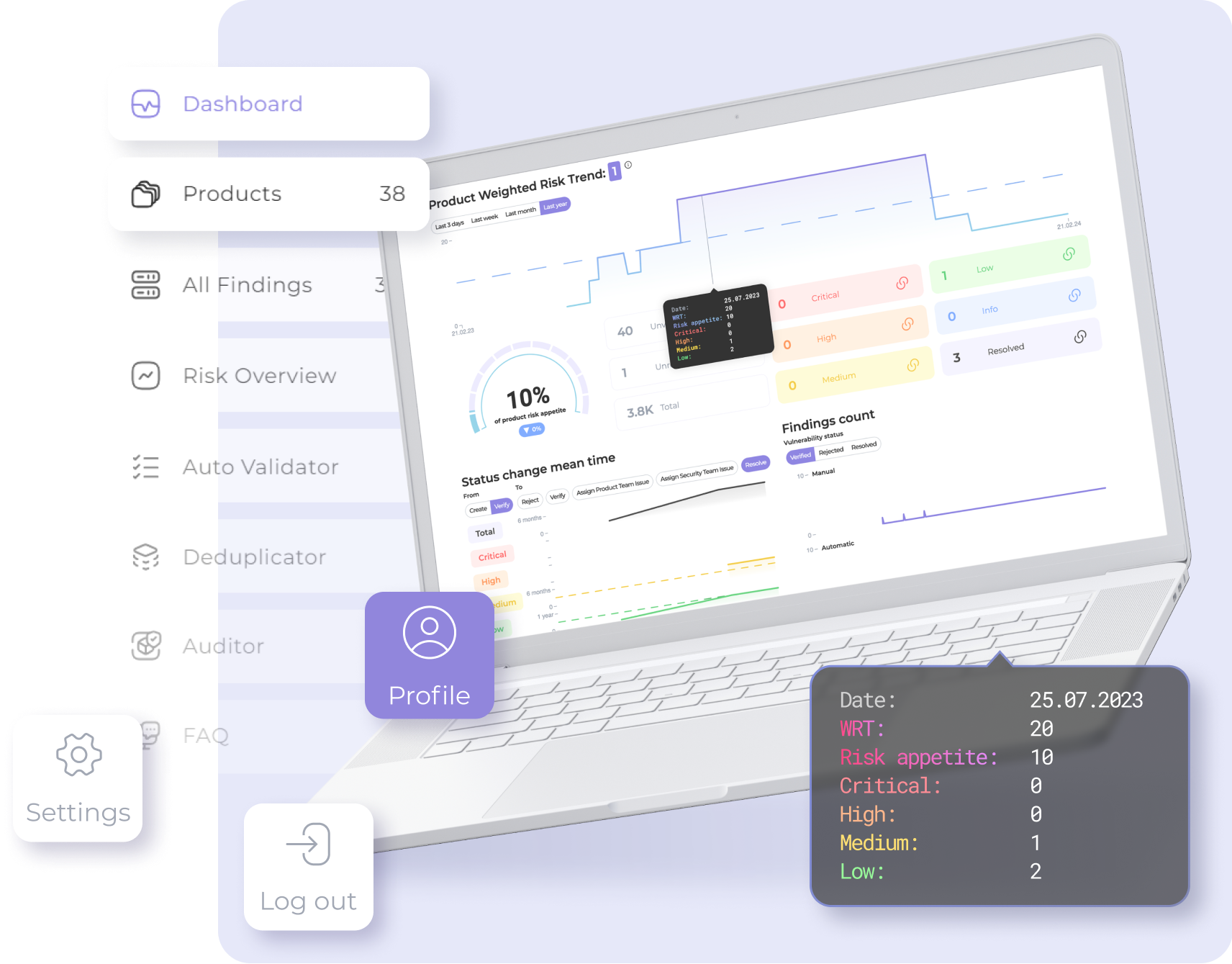


Convenient monitoring panel and visual reports
Compatible with security standards



Let's discuss the details of your project on a free consultation
Leave a request, and our specialist will contact you
to arrange the first online meeting
to arrange the first online meeting
We work with various
niches
Foreign Exchange

Problem:
Customers data were not properly secured by design

What’s now:
Continous internal security checks, measured weighted risk trend
Payment systems

Problem:
Lack of vulnerability discovery and management process for PCI DSS

What’s now:
Continous internal security checks, measured weighted risk trend
Delivery

Problem:
Enhance the level of customer
data protection
data protection

What’s now:
Continous internal security checks, measured weighted risk trend
Cloud Hostings

Problem:
Prevent abuse of corporate resources and cryptocurrency mining

What’s now:
Continous internal security checks, measured weighted risk trend
Ed-Tech

Problem:
Protect company's developed courses from being breached

What’s now:
Continous internal security checks, measured weighted risk trend
Product information gathering
The initial stage includes a deep analysis of the current security status of your products. We assess all of your product features
to identify potential threats
to identify potential threats
Vulnerability discovery
The next step is to search for all possible vulnerabilities.
Our team carefully identifies weaknesses that can be exploited
by attackers to fulfill their motivation
Our team carefully identifies weaknesses that can be exploited
by attackers to fulfill their motivation
Detailed report with recommendations for elimination
Once vulnerabilities are identified, we provide clients with detailed recommendations for their elimination. We will guide your developers on how to implement all fixes, so you could be sure that they are corrected properly
Discussion of changes in the development process
For assurance that new vulnerabilities do not appear,
we consult with clients and their team of specialists. Our team will explain in detail what needs to be changed in the development process to avoid problems
we consult with clients and their team of specialists. Our team will explain in detail what needs to be changed in the development process to avoid problems



Let's dive into the details
during a free consultation
during a free consultation
Just leave your request and our experts will explain how we can help you during the free consultation
What people
Clients from various fields - from financial services to IT technologies - confirm the effectiveness of our work
say about us



Sergey Nozhenko
Information Security Engineer
Using Application Security portal was a breath of fresh air. The guys follow an agile approach with stable releases and adding new features

Bogdan Panasiuk
It sec manager
The best product for vulnerability management. It has a good interface, works fast (even if has more than 100 added products/projects and 500k findings). My favorite feature is deduplication. The portal merges results from different scanners and can reject findings according to preset and custom rules. This feature saved a huge amount of time for me and my colleagues
Dmitry Donchenko
data scientist
Recently tried this new security platform and I'm liking it. It's easy to use and great for handling vulnerabilities in app development. A solid choice for anyone in security.
Whitespots team
To protect your business from constantly changing threats, we have gathered cybersecurity experts at Whitespots. All members of our team have extensive experience. They possess technologies and knowledge in different niches and apply
a comprehensive approach to secure your assets
a comprehensive approach to secure your assets
specialists

In our team:

10
cybersecurity experts

5
managers
Maxim Mosharov
CEO

